Digital Privacy for the Discerning
Take Control of Your Digital Exposure
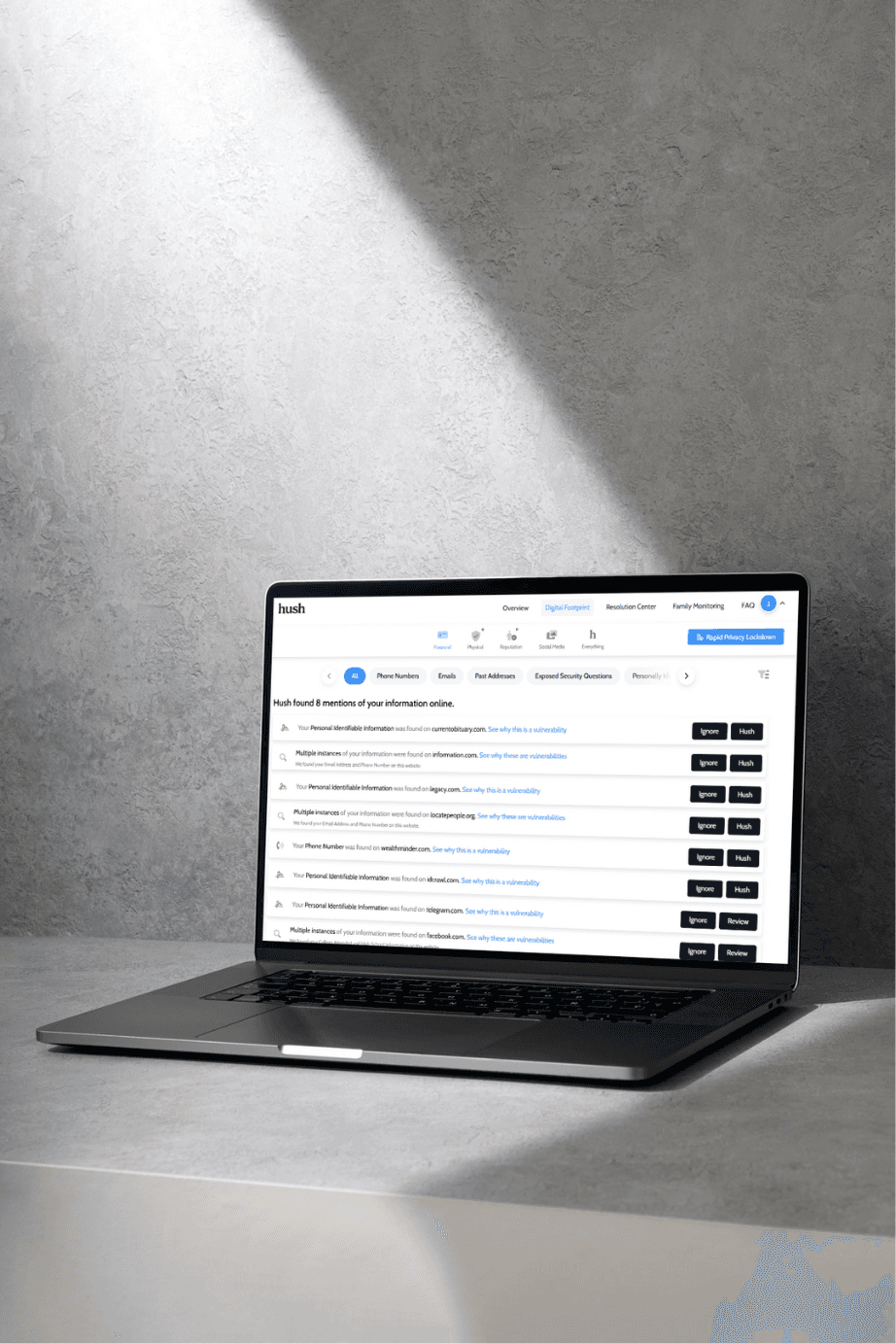
Executives and high-net-worth households operate in visible environments. Hush — the leading data removal company for UHNW individuals — identifies and removes personal information from data brokers, public records, and search results, then continues managing your exposure with dedicated stewardship.
Safeguarding the World’s Most Distinctive Brands
Trusted by family offices, private equity firms, and the world’s most discerning institutions to protect what matters most.


Our Services
Select the Service You Require
Hush operates across two distinct disciplines. Identify which best fits your situation and let us build a protection plan around you.
Digital Executive Protection
Comprehensive threat monitoring, data broker removal, and digital footprint suppression for executives, public figures, and high-value targets who require continuous, proactive defense.
Private Client Services
White-glove privacy management for UHNW individuals and their households — removing personal information, protecting family members, and maintaining discretion at every level.
The Hush Standard
Hush is your concierge — present when needed, invisible when not, and devoted entirely to one priority: yours.
98%
of cyberattacks involve exposed personal data.
320M
people were affected by cyberattacks in 2024.
58x
a CEO is targeted by a phishing attack.
700x
a year, the average organization is attacked.
Resources
White Paper & Report
Personal Risk Is Enterprise Risk
This whitepaper explores how executive digital exposure creates measurable institutional risk — especially during high-stakes moments like M&A, capital raises, and leadership transitions. It reframes leadership privacy as preventative risk infrastructure.
White Paper & Report
Why Executives Are Easy Targets
While many organizations focus heavily on protecting systems and networks, they often overlook a major security risk: executives themselves. Senior leaders are highly visible and digitally exposed, making them high-value targets for attackers.
White Paper & Report
Executive Protection to Organizational Safety
This paper outlines why Hush creates multiplicative — not incremental — value when deployed across the wider employee population, and how large-scale adoption transforms individual protection into operationalized organizational safety.
Private Client Services
We Are Entirely at Your Disposal
Our private client team is available around the clock — ready to advise, respond, and act with complete discretion and without delay.
Featured In